SonicWall NSa 3700 – Advanced Networking for the Advanced Threat Era
SonicWall NSa 3700 firewalls are designed to secure mid-sized businesses, distributed enterprises, and large branch office locations while delivering performance superior to even recent generation firewalls. Featuring SonicWall’s SonicOS 7.0 operating system and its slew of new management and control features, the NSa 3700 sets itself apart from its NSa firewall predecessors.
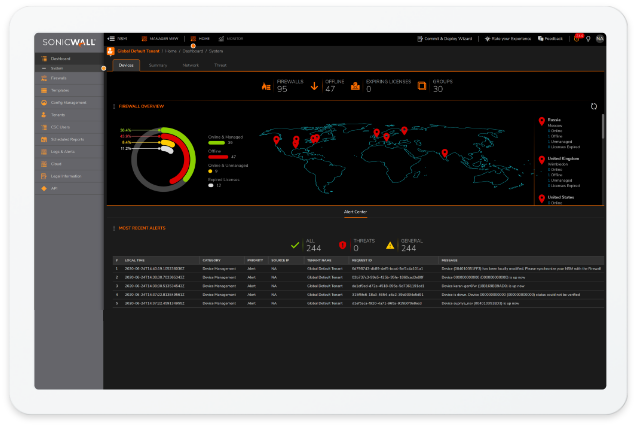
The SonicWall NSa 3700 is ready to tackle SD-WAN deployments, security layer clustering, high-speed remote access through site-to-site and DPI SSL VPN, and more. In addition, the SonicWall NSa 3700 enables admins to monitor and manage all network traffic through a simple dashboard interface that prioritizes displaying fast, intuitive information right up front.
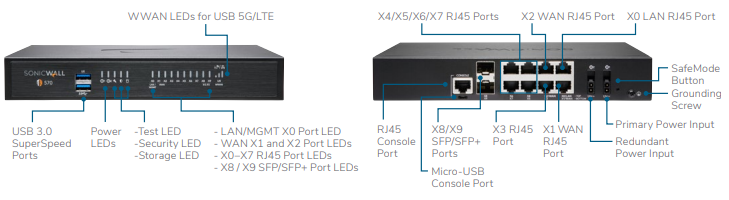
With multi-gigabit threat prevention throughput and super fast encrypted traffic scanning, you won’t lose all the bandwidth and speed you pay out to your ISP each month. On top of that, the SonicWall NSa 3700 features physical upgrades as well: 24 Gigabit ports, 6 10-gig ports, and 4 SFP+ ports capable of working on a 5G network.
























































































SonicWall NSa 3700 Spec Snapshot


SonicWall NSa 3700 Next Generation Firewall
Max Firewall Throughput: 5.5 Gbps
Threat Prevention Throughput: 3.5 Gbps
Application Inspection Throughput: 4.2 Gbps
Network Interface Ports: 24x1GbE, 6x10GbE, 4x5G SFP+, 2 USB SuperSpeed 3.0, 1 Console, 1 Management
DPI Maximum Connections: 750,000
Connections per Second: 22,500
VLAN Interfaces: 256
Site-to-Site VPN Tunnels: 3000
Hardware-Only MSRP: $4095
View the SonicWall NSa 3700 Datasheet
Check out our latest video on the SonicWall NSa 3700:
What’s New in SonicOS 7.0?
SonicWall’s Gen 7 firewalls feature a brand new operating system that simplifies network security management while focusing on the most pressing threats facing small businesses. TLS 1.3 decryption aims at hunting down and snuffing out elusive encrypted threats. This increased visibility is right at your fingertips. The SonicOS Capture Threat Assessment Report provides summarized insights into traffic, applications, and a variety of advanced threats, ensuring you know exactly what’s lurking on your network.
The learning curve for SonicOS 7.0 is extremely user-friendly, with auto-provision VPNs and the SonicExpress app that make zero-touch deployment a reality. In the era of remote work, the ability to quickly and easily deploy a high-performance, high-security appliance without needing a technician at each site is crucial.
Check out our article SonicOS 7.0: 7.0 Reasons Why This SonicWall OS Rocks to learn more.
























































































TotalSecure Advanced Edition & Essential Edition
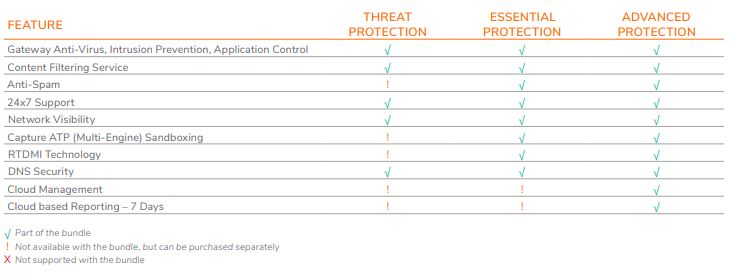
So many new advanced features and services arrived with the SonicOS 7.0 appliances that SonicWall had to make brand new licensing bundles to house them all. With the NSa 3700, you have two bundle options. The more basic bundle, called the TotalSecure Essential Edition Bundle, includes these SonicWall security services:
- Gateway Anti-Virus, Intrusion Prevention, Application Control
- Content Filtering Service
- 24×7 Support
- Network Visibility
- Basic DNS Security
- Anti-Spam
- Capture ATP (Multi-Engine) Sandboxing
- RTDMI Technology
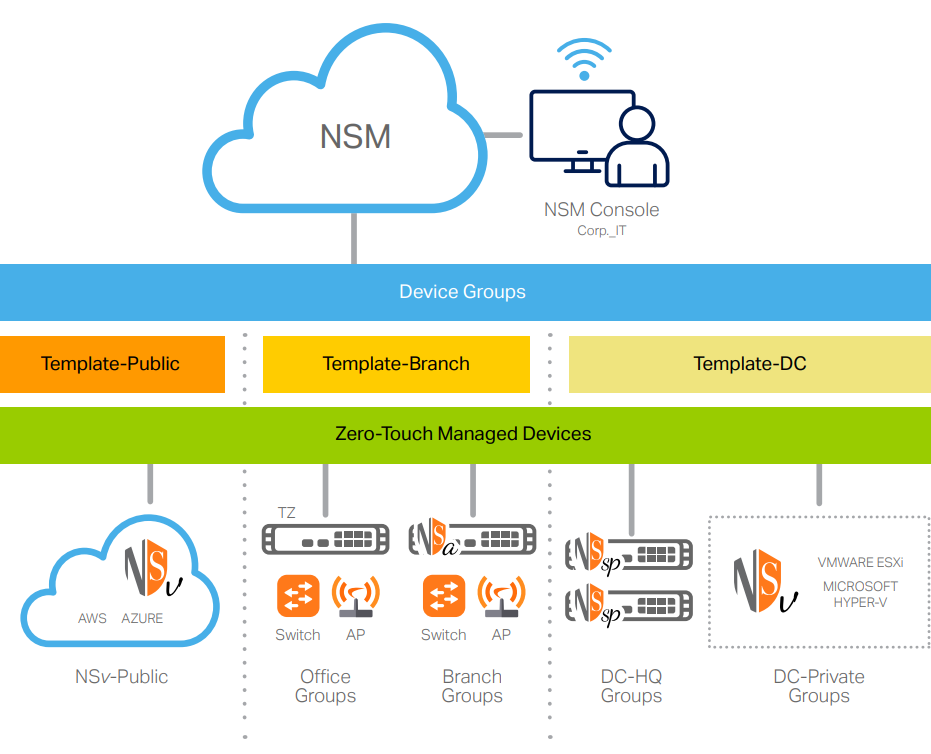
The TotalSecure Advanced Edition includes everything in the Essentials Edition, with the added bonus of SonicWall Network Security Manager (NSM) Essentials. NSM features:
- Cloud Management
- 7 Days Cloud-based Reporting
Optionally, services can be purchased a la carte as well.
Looking for More Firewall Solutions from SonicWall?
Shop SonicWall NSa firewalls if you’re looking for enterprise-grade protection at SMB prices.
Future-proof your setup with secure, scalable SonicWall Network Switches.
Or browse all of our SonicWall products to find the perfect solution for your unique network needs.