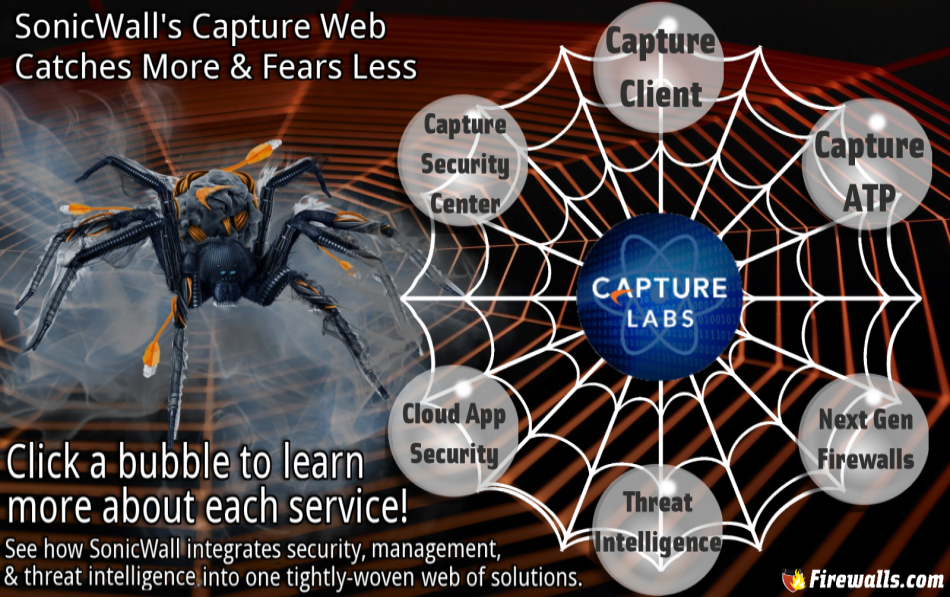
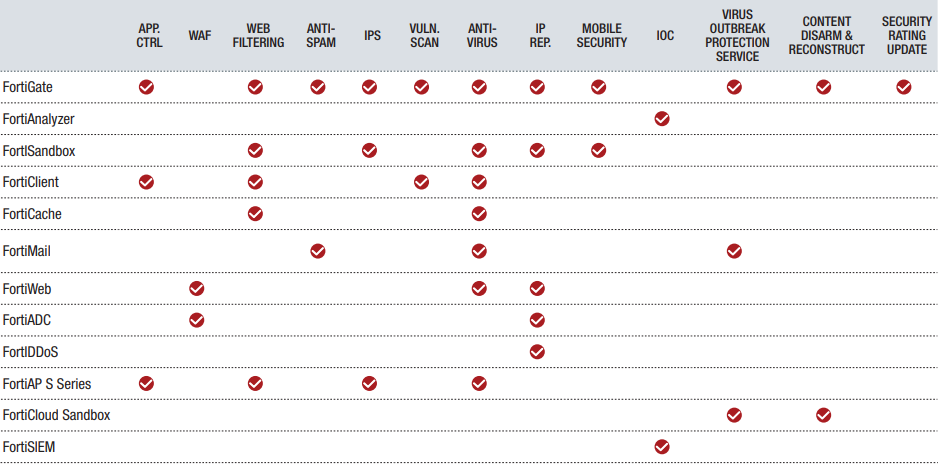
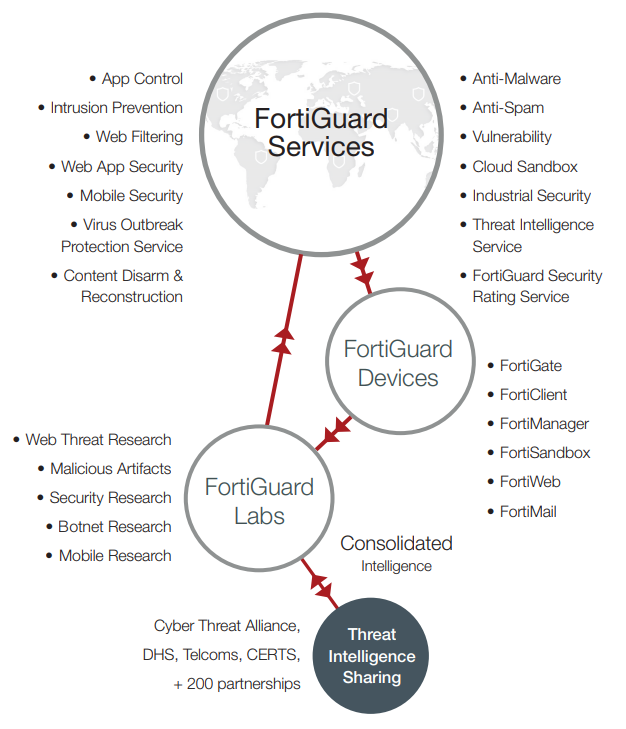
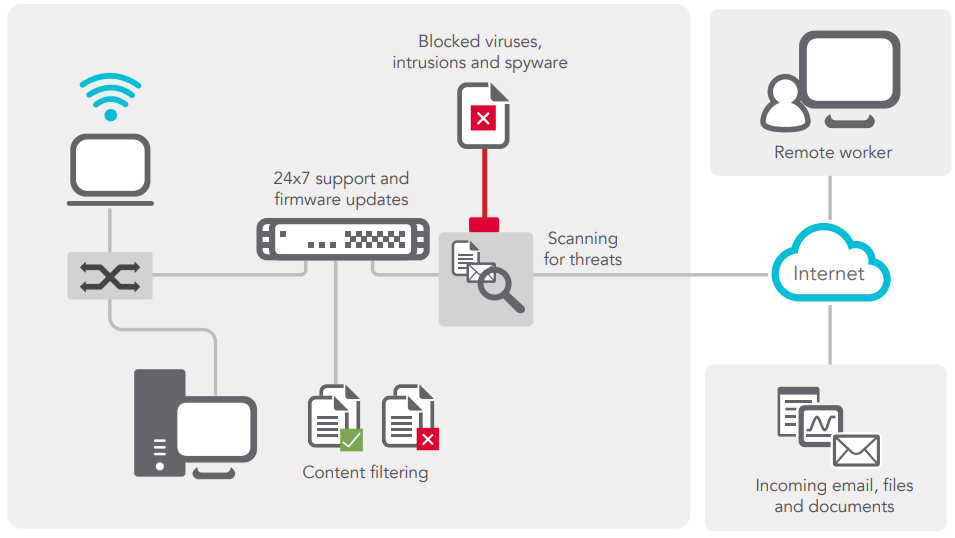
The 2018 SonicWall Cyber Threat Report was just released and we’re here to break down this massive report into bite-size morsels for you to chew on. Each year, SonicWall Capture Labs publishes an in-depth look at the trends, changes, & tech that shaped the cyber threat landscape over the previous year and they use their findings to predict the volatile threat landscape that organizations can expect to traverse in the coming year. Predict your own cyber security future by understanding these 5 key takeaways from the 2018 Cyber Threat Report.
1. Ransomware
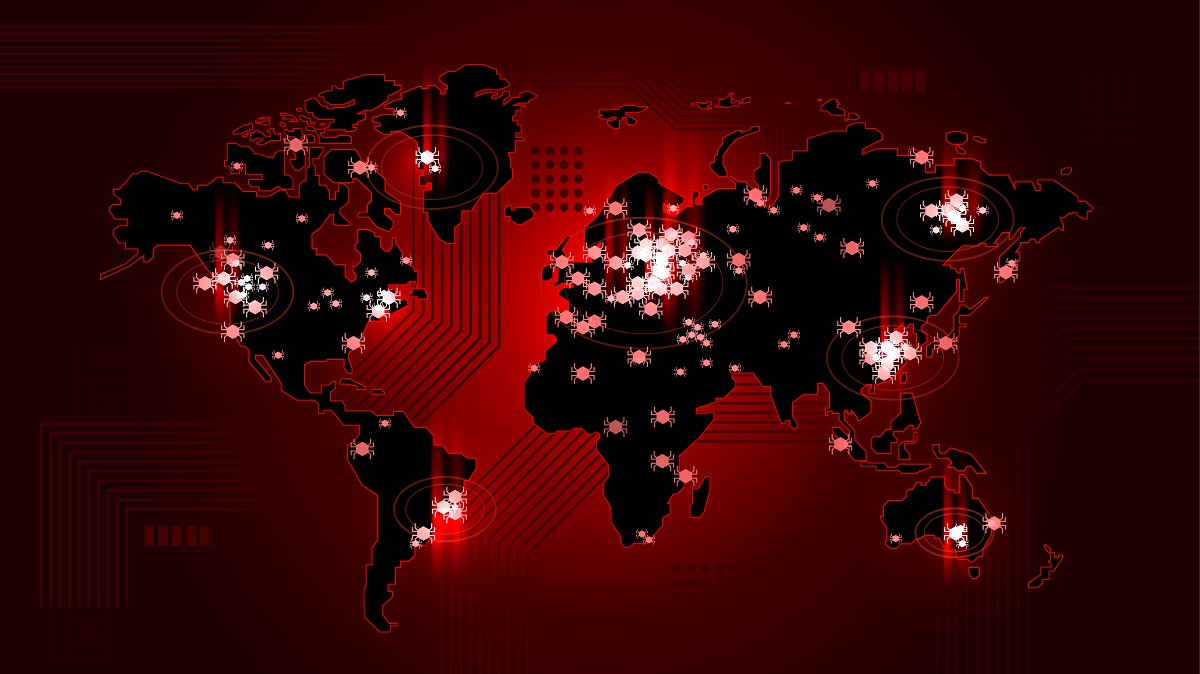
Wave goodbye to the cyber security war that you once knew. No, it’s not over. It’s just a little different now. Despite headline-worthy attacks rocking Europe and North America, 2017 was a year of retreat and regroup for threat actors. No longer happy to play the numbers game, criminals have instead turned their focus towards innovation. While overall ransomware attacks dropped, the number of unique variants increased in 2017.
The number of ransomware attacks detected in 2017 by SonicWall Capture Labs totaled 183.6 million, a 71% drop compared to 2016. Nonetheless, of those detected hits, SonicWall discovered one never-before-seen variant for every 250 known threats it encountered. This means that ransomware is becoming more versatile. In 2018, expect the trend to continue, meaning your organization will be defending from fewer attempts, but each attempt will be smarter and more cunning than previous years.
What does this mean for me?
If you’re not already using a cloud-based sandbox, 2018 is the year to jump on the wagon. Zero-day threats may well become the new norm, meaning you’re only partially protected if you still depend on signature updates and patches. As the threat landscape shifts from quantity to quality, it is paramount that organizations stay ahead of the wave.
2. Malware
Where ransomware has taken a step back to catch its breath, malware filled the void in 2017, rebounding from the significant dip witnessed in 2016. From 2015 to 2016, malware attacks dropped from 8.19 billion occurrences to 7.87 billion, a statistic initially interpreted as a signal that malware was on the decline. 2017, however, saw a roaring return with over 9.32 billion malware attacks logged by SonicWall Capture Labs.
Malware in 2017 did have some unique features compared to past specimens. With the fall from grace of Adobe Flash sweeping a huge category of vulnerabilities and exploits into the trash, malware authors designated Microsoft as their new punching bag. Attacks against old targets like Acrobat Reader and Reader DC are down. Meanwhile, attacks targeting Word, Excel, and other Office products are ramping up.
Second, threat actors have seemingly joined the green movement by making recycling a big aspect of malware lifecycles. No, we’re not talking about scraps of trash, but malware code itself being reused, rehashed, and rewritten. The SonicWall Cyber Threat Report refers to this phenomenon as “malware cocktails.” Such cocktails are created by mixing and matching snippets of code or functionality from several malware kits and splicing them into new Frankenstein-esque creations.
What does it mean for me?
Take your signature-based scans and toss them out the window. It’s high time you switch over to behavior scanning. Most cyber security brands worth their weight are relying more heavily on machine learning, deep system scans, and real-time protection. Both SonicWall’s Capture ATP & Sophos’ Sandstorm make use of the latest deep learning capabilities to identify, probe, and judge data in fractions of a second. Much like our response to ransomware above, the key to steering clear of a malware infection will be in an organization’s ability to stay dynamic.
3. SSL/TSL
Speaking of malware, another important shift in the threat landscape is malware’s ability to hide itself behind encryption. Encryption, specifically through SSL/TSL protocol, has accelerated, with over 60% of web traffic now encrypted. Soon, Google Chrome will begin marking all unencrypted pages as “not secure.” All signs point towards a future where SSL/TSL secured sites are the normal and malicious traffic is no exception.
What does it mean for me?
According to the report, organizations that lack the ability to inspect encrypted traffic missed, on average, over 900 attacks hidden by SSL/TSL encryption in 2017. In addition, many attack kits are leveraging custom encryption languages, making it even more problematic to parse out their payload.
Stateful inspection and bad policy configuration are no longer effective if you want to catch all of the attacks. In 2018, an organization will rely heavily on its ability to inspect encrypted traffic. It may be wise to get a second set of eyes to review your NGFW configuration to ensure your network is set up to deal with encrypted threats.
4. Internet Of Things
We wrote up a comprehensive article on IoT in 2017 that takes an in-depth look at the developments and dangers surrounding the Internet of Things. Since then, exploits with very scary names such as Meltdown and Reaper have emerged. Unfortunately, IoT-enabled products continue to be produced with little to no regard for cyber security. Expect to see the weaponization of IoT clusters for use in botnet DDoS attacks.
What does it mean for me?
Honestly, we’re not sure. The bad guys have not yet figured out how to best make use of this emergent attack vector. Whatever the future may hold for IoT, one thing we know for certain is that we will one day regret the short-sightedness of pumping all of these network-enabled devices into public hands with scant oversight of security risks. SonicWall Capture Labs has put forth at least one solution, which we’ll outline next.
5. Real-Time Deep Memory Inspection (RTDMI)
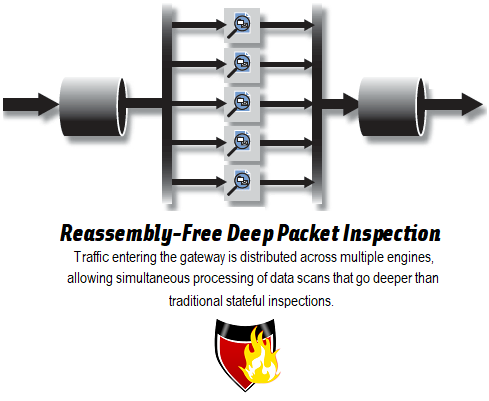
SonicWall has demonstrated its inventiveness over and over throughout the years with a strong portfolio of patents. Most notable is their patented Reassembly-Free Deep Packet Inspection, a method that allows simultaneous scanning of data chunks through multiple processing engines, changing DPI services of old from bottlenecks into high-speed security checkpoints. In 2018, SonicWall continued their proud tradition of innovation by opening new battlegrounds in the fight against cyber crime in advanced technologies such as IoT, chip-based threats, & mass market malware with the introduction of their patent-pending Real-Time Deep Memory Inspection.
There’s not a whole lot of information about RTDMI released so far, but the few snippets of features we were able to find hinted at potential capabilities. RTDMI is located in the Capture cloud and has been quietly operating for a few months now, so if you’re currently running Capture ATP you’re already under RTDMI’s silent watch.
RTDMI can detect and block malware that conceals its malicious behavior behind encryption. By scanning these encrypted threats in real time and forcing them to expose their intentions in processor memory, RTDMI promises to root out even the best disguised attacks. According to the threat report, the act of exposing, detecting, and blocking these kinds of advanced threats takes place in a timescale of under 100 nanoseconds.
What’s this mean for me?
Again, we’re not sure yet. But you should find this news reassuring at the least. RTDMI demonstrates that SonicWall is already working to solve the emerging threats of tomorrow. We’ll keep bugging SonicWall for more information on and we’ll let you know what we find out about this mysterious new patent-pending tech.
There is one common thread linking all of this information: set-it-and-forget-it is dead. Cyber safety in 2018 equates to dynamic, real-time, advanced tech focused efforts. Still relying on a legacy firewall or bare bones subscriptions? We recommend you start weighing your options. And if this all sounds expensive to you, consider softening the upfront costs by partnering with a Security-as-a-Service team where everything you need to stay secure is provided at a much lower cost monthly subscription.
READ THE FULL 2021 SONICWALL CYBER THREAT REPORT