One of the world’s largest global data centers has announced an investigation into a ransomware incident. On Sept. 9th, Equinix – which directly connects to AWS, Google Cloud, Azure, Oracle, and AT&T – revealed the inquiry. It’s been a rough few weeks for enterprise organizations and ransomware. Less than a month ago, we saw a thwarted breach of Tesla which could have commanded a massive ransom. Below is an official statement from Equinix.
“Equinix is currently investigating a security incident we detected that involves ransomware on some of our internal systems. Our teams took immediate and decisive action to address the incident, notified law enforcement and are continuing to investigate. Our data centers and our service offerings, including managed services, remain fully operational, and the incident has not affected our ability to support our customers. Note that as most customers operate their own equipment within Equinix data centers, this incident has had no impact on their operations or the data on their equipment at Equinix. The security of the data in our systems is always a top priority and we intend to take all necessary actions, as appropriate, based on the results of our investigation.”
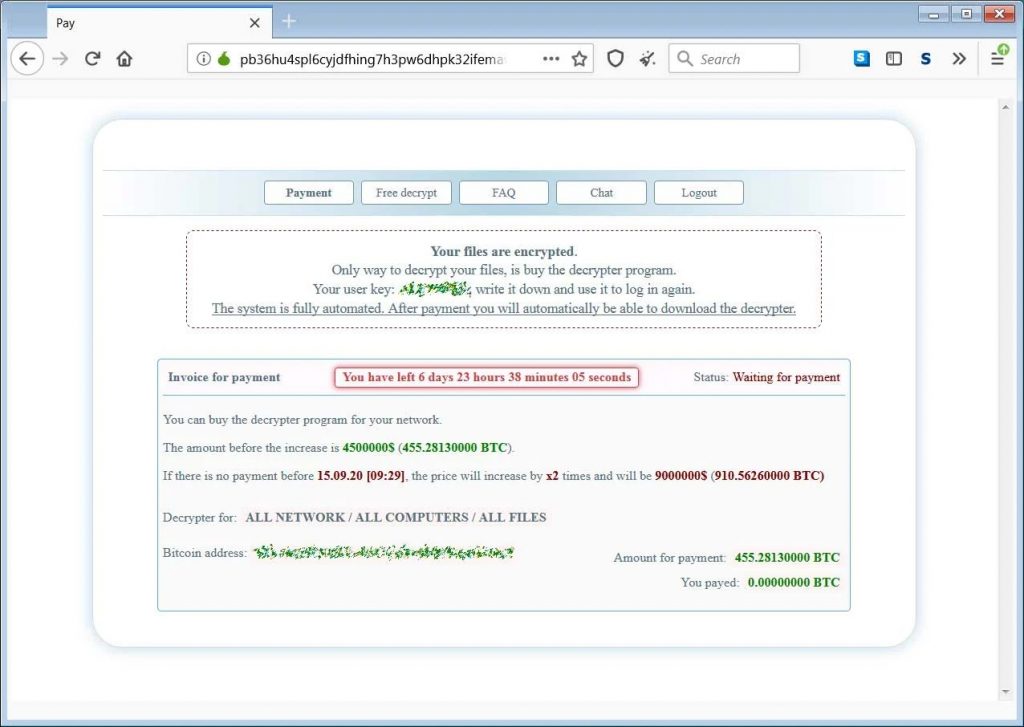
Equinix was reportedly hit with a Netwalker ransomware attack in which attackers asked for $4.5 million, threatening to release stolen data to the public. If 7 days lapse without payment, Equinix will face double the ransom amount. It’s not hard to imagine these guys are scrambling right now, assessing all their options.

From photos released to the public by the hacking group, it seems data centers in Australia were the weak points for the breach. The information stored in those data centers may also be what’s at risk of exposure.

About Equinix
Equinix is a global data center headquartered in Redwood City, California. Leadership of the organization includes CEO Charles Meyers and Founder Jay Adelson. Equinix is a publicly traded company on NASDAQ (EQIX). With revenue hitting $5.5 billion in 2019, Equinix is a major player in the global data center industry.
Learn More About Ransomware
Don’t be the next victim of a ransomware attack. Strong cloud-based sandboxing, frequent firmware updates, & smart network security practices can keep you secure.






