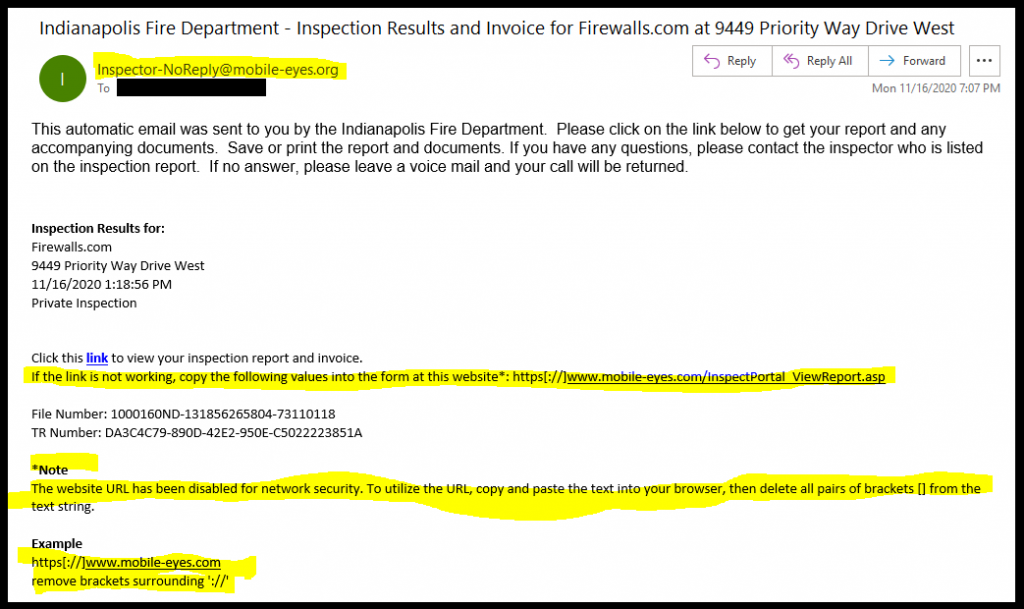
The local fire department is reaching out to let our small business know that we’ve passed our inspection. Very important! Or is it? Let’s take a close look at an innocuous email that slipped into a Firewalls.com inbox in an article we’re calling “Anatomy of a Phishing Email.”
How phishing attacks work
Building false trust – The above email was definitely targeted. By providing accurate information about our company, street address, and employee names, this attacker was attempting to build trust with the recipient. Social engineering attackers often attempt to impersonate legitimate mail senders by doing pre-emptive research on their targets.
Setting the bait – Phishing attackers are always on the lookout for some theme to build their scam around. This bait often relates to trending news topics, routine business processes, or impersonating someone you know. In this example, our phisher relied on quarterly fire inspections in an attempt to trick our recipient. Fire inspections are routine, but infrequent enough that the average employee will not have much knowledge about their last checkup. On top of that, the setup sounds critical to everyday business operations at first glance.
Springing the trap – Fortunately, our team was quick to spot the fake. This attacker wanted our recipient to visit a certain URL where something far more nefarious lies in wait. Here, the attackers provide a hyperlink that they know will not function properly and provide further instructions to manually enter a URL, rerouting victims to their intended trap.
How can you spot a phishing attempt?
There are several questions you should ask yourself if you think you may be the target of social engineering. Here are a few things that stuck out to Firewalls.com that made us suspicious.
Sender legitimacy – Is your local fire department really going to send you an invoice by email? Have you ever received an email from this person/organization before? Most businesses and institutions won’t suddenly reach out to you via a new platform without some warning first. If the legitimacy of the senders gives you pause, you may be a target!
What information do they know about me? – Building trust by personalizing phishing emails to their target is common sense. You are more likely to believe hackers’ schemes if they seem to have accurate information about you. However, what exactly do they know? In this case, our attacker seems to know an email address, company name, and a physical address. Impressive at first sniff, but this is all publicly-available information! Never take the bait just because it has your name on it.
What is being asked of me? – While the initial setup seems believable enough, this ruse starts to fall apart when you peel back the layers. Why would the fire department send me a link that they know is broken? Why send complicated instructions on how to manually edit URLs to work around a defunct web portal?
Does it all match up? – If an email says it is from the local fire department, but the send domain contains something completely unrelated (mobile-eyes?), you may be onto something! In this example, the attacker is instructing our recipient to visit a web domain that has nothing to do with fire inspections. More like “mobile-eye-don’t-think-so.”
What to do if you think you received a phishing email
Never spring the trap – First and foremost, do not click anything! Links, attachments, replies, forwards—leave it all alone. You cannot be breached simply by receiving the email, so stop while you are ahead.
Get IT involved – Alert your IT team and immediate supervisors. If you have even an inkling of doubt about the legitimacy of an email, there’s no harm in getting a second opinion from an expert. Reach out to your IT department for further guidance.
Block the sender – If this is just one attempt in a more persistent or complex spearphishing campaign, there will be further emails brewing. Blocking the email domain of a bad actor prevents a future lapse in judgment or mistake from providing a second point of entry for foiled attackers.
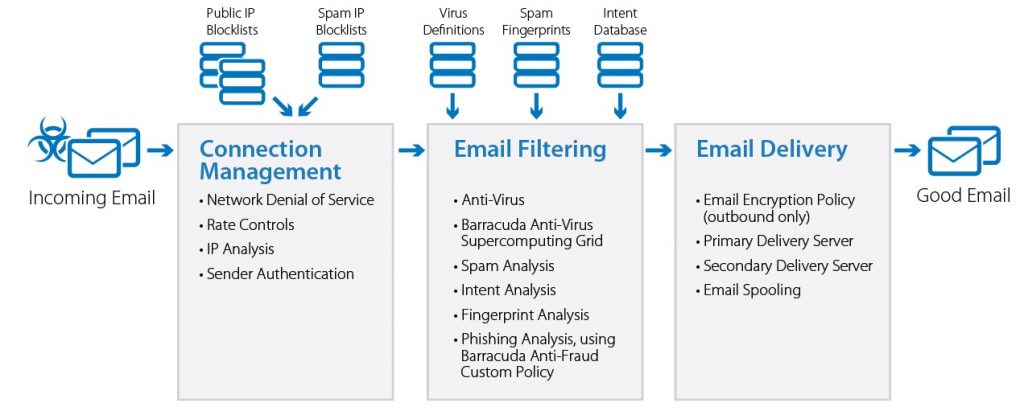
Rely on defense-in-depth – Want to know the easiest way to sidestep an attempted phishing scam? Do not let it ever land in your inbox. Defense-in-depth network security strategies employ email encryption, cloud-based sandboxing, and Time-Of-Click protection to provide email security before, during, and after delivery of suspicious messages. Tools such as SonicWall Capture Advanced Threat Protection and Barracuda Essentials take the guesswork out of checking your mailbox.

Ransomware and malware delivered through phishing emails are more rampant than ever before. Whether hackers are relying on coronavirus scams, election news, Black Friday deals, fire inspections, or otherwise, there’s always some new social engineering scheme on the horizon. Protecting yourself starts with educating yourself against these attacks. Stay safe while holiday shopping by tuning into our podcast episode “Black Friday Becomes Cyber November 2020” featuring Dan Lohrmann.


Want to learn more about phishing and social engineering?
Check out our podcast on Phishing with SonicWall’s Matt Brennan.
Check out our Firewalls.com Threat Dictionary entries on ransomware, phishing, and spearphishing.




