Best Endpoint Security of 2020 for Your Small Business
Finding the best endpoint security for your network needs can be a challenge. There are dozens of options, all supporting a myriad of advanced security features and integrations that may be impossible to navigate unless you’re an expert. Each vendor offers a unique set of services with strengths and weaknesses that will ultimately determine whether your users stay safe or not. The best endpoint security may vary from organization to organization, but here are our top picks for the best endpoint security options available in 2020.
What is Endpoint Security?
Endpoint security, end user security, endpoint protection—while the name can be flexible, its necessity for a secure network is not. Endpoint security software protects small businesses & enterprises by guarding connected devices against malware and other advanced cyberattacks. Modern endpoint security integrates with appliances and applications you already use to provide edge protection as employees and guests access your network.
Encrypted malware, ransomware, and business email compromise can spell disaster for small businesses. That’s why the ability to monitor end user activity in real time – as well as make decisions to quarantine and isolate individual machines – can mean the difference between a small, contained incident and a catastrophic breach.
In 2020, endpoint security platforms now incorporate Endpoint Detection & Response capabilities powered by AI. Guided response, rich reporting, and root cause analysis are all top-shelf features that organizations should seek in a quality endpoint security service.
What does Endpoint Security include?
The best endpoint security goes beyond the basics. Traditionally, end user protection included passive endpoint scans combined with basic antivirus capabilities. However, in 2020, the best endpoint security blow the basics out of the water with multiple advanced security features:
- Continuous monitoring of files, applications, & connected devices
- Automated incident detection and isolation of infected machines
- Web content filtering to safeguard productivity and network usage
- Auto-provisioning based on user group, OS, location, or time of day
- Intuitive regulatory compliance controls & reporting
- Real-time threat intelligence updates from a pedigreed threat research team
The threat landscape is always evolving. That means your end user protection must stand up to threats never-before-seen by the network security ecosystem. The ability to recognize zero day exploits based on machine learning and behavioral analysis is essential for organizations to stay secure in 2020.
What is the Best Endpoint Protection of 2020?
Here are our top picks for the best Endpoint Protection for small businesses in 2020:
SonicWall Capture Client
Key Features:
- Continuous behavioral monitoring creates complete profile of network activity
- Layered defense of cloud intelligence, advanced static analysis, & dynamic protection
- Integration with Capture Advanced Threat Protection cloud-based sandboxing
- Ability to rollback targeted endpoints to a restored state even after infection
- Malware protection engine powered by SentinelOne
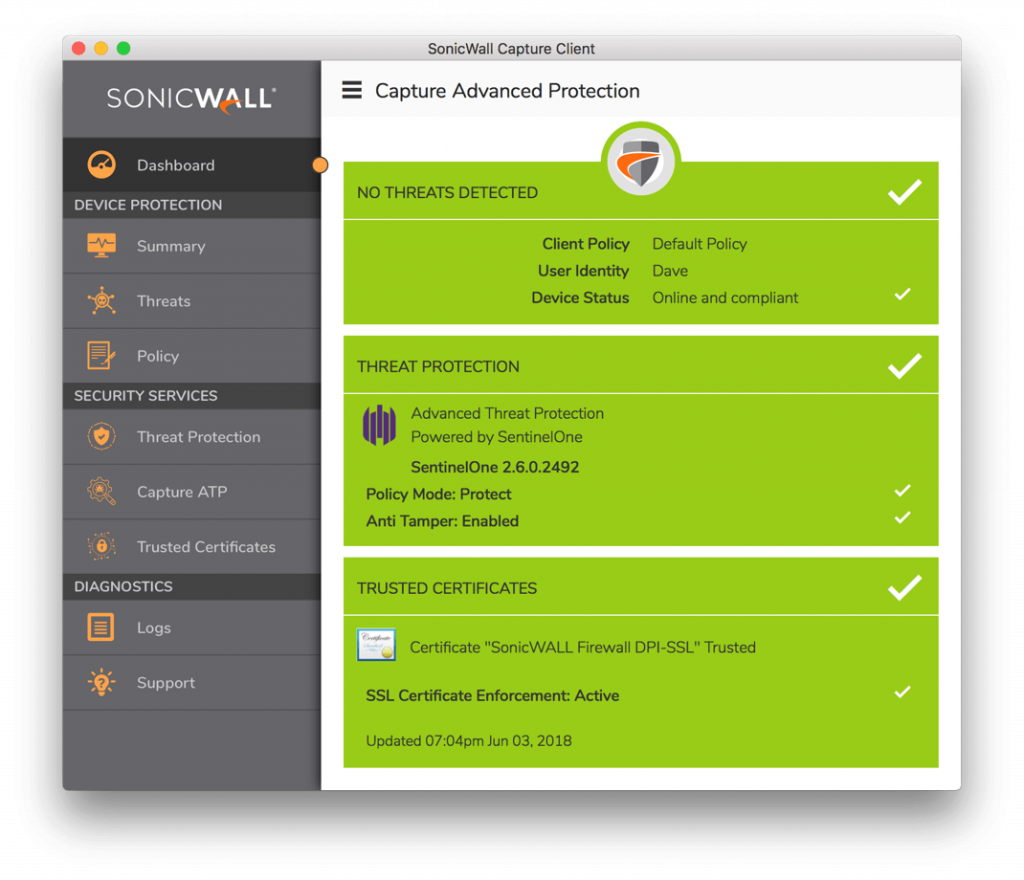
What makes SonicWall Capture Client unique?
SonicWall teams up with SentinelOne to deliver a heuristic endpoint protection suite with the unique capability to mirror Microsoft shadow copies for post-infection rollbacks. This eliminates the need for manual restoration after a ransomware attack and lets admins rest easy knowing they can always restore endpoints to their pre-infection state. In addition, round-the-clock behavioral monitoring eliminates the need for scheduled system scans. In short, this minimizes network resource hogging and safeguards user productivity.
Fortinet FortiClient
Key Features:
- Integrates with all Fortinet Security Fabric components
- Automated prevention of known & unknown threats through host-based security stack
- Intelligent patch management & vulnerability shielding
- SSL & IPSec VPN security provides reliable access to corporate networks
- Detects elusive memory techniques used in exploits like buffer overflows
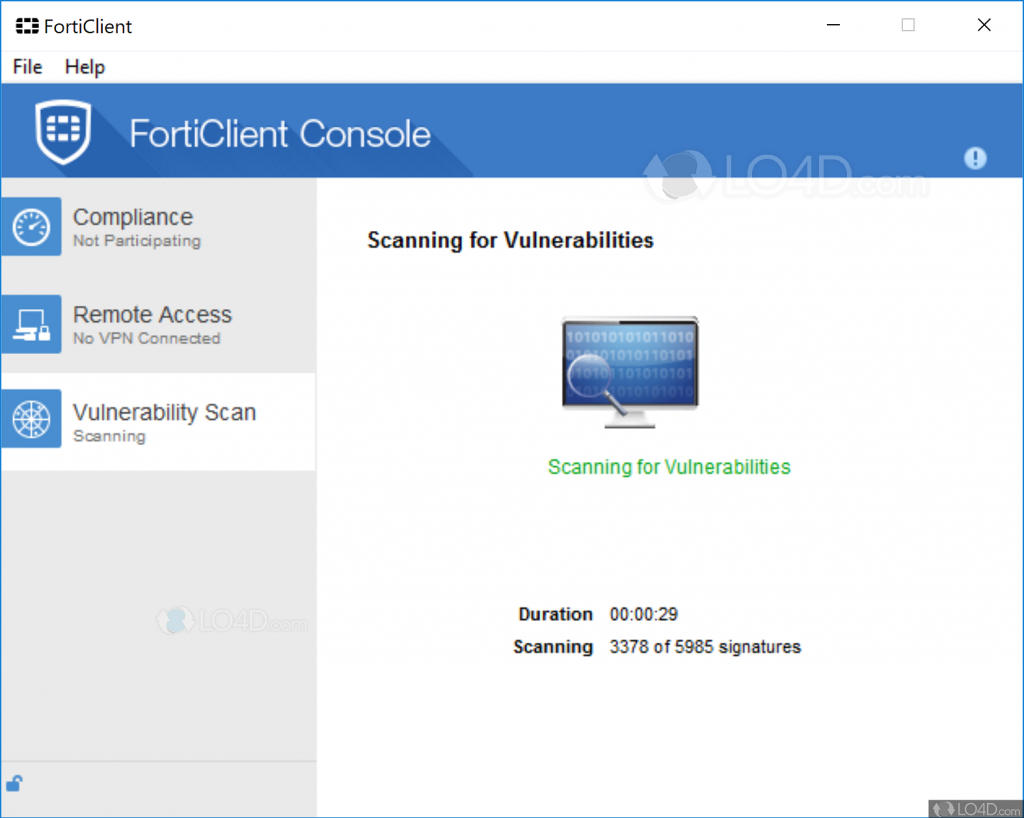
What makes Fortinet FortiClient unique?
Fortinet FortiClient end user protection services simplify remote user experience with built-in user provisioning, auto-connect, and an “always-up” VPN. FortiClient works perfectly in tandem with all Fortinet devices and services on your network through the Fortinet Security Fabric. According to NSS Labs 2019 Advanced Endpoint test, FortiClient blocked 100% of malware including extremely elusive threats.
Sophos Intercept X Advanced with EDR
Key Features:
- Automatically detects, prioritizes, & investigates potential threats using AI
- Leverages deep learning analysis to analyze malware in extreme detail
- Out-of-the-box SQL queries categorized by use case
- Live Response provides users command line access to endpoints & servers
- Quickly search up to 90 days of current & historical on-disk data
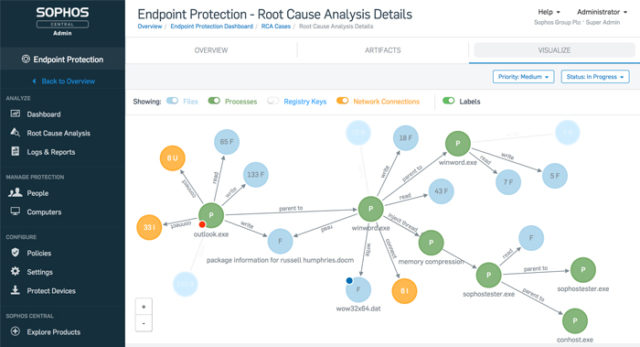
What makes Sophos Intercept X Advanced with EDR unique?
Sophos made a huge splash with the upgrade to its original Intercept X service. It sports big changes that included Endpoint Detection & Response (EDR) capabilities in addition to its already robust real-time, integrated endpoint platform. Intercept X Advanced combines powerful endpoint protection with endpoint detection driven by machine learning. This means most threats are squashed long before they can damage your network. Artificial intelligence assists with guided response. To save your small business even more, an important note: the objective of Sophos endpoint protection is to reduce the need for added IT employees by consolidating their roles into a single automated system.
Cisco Meraki Systems Manager
Key Features:
- Native Network Integration shares intelligence across all Meraki components
- Automatic WiFi settings securely connect managed wireless devices
- Auto-provisioning of VPN settings based on Client VPN
- Zero-touch deployment through a self-service web portal
- Deploy policies & changes from the cloud across the entire network
What makes Cisco Meraki Systems Manager unique?
Cisco Meraki’s endpoint management solution supports a variety of platforms and operating systems, making Systems Manager a flexible option for most any deployment. Systems Manager offers cloud-based endpoint management tools that easily scale up to meet growth needs. By providing admins the ability to manage distributed deployments from anywhere in the world, Systems Manager is an endpoint security solution built for a highly mobile, highly distributed world.
Look for the best endpoint protection for your small business?
Give us a call at 866-957-2975 to find the perfect fit!