What are Sophos Threat Cases?
Sophos Threat Cases make Intercept X Advanced with EDR truly stand out from the crowd as an end user protection platform. Granting admins the ability to investigate and clear up malware attacks with just a few clicks, Threat Cases provide a birds’ eye view allowing you to visualize incidents occurring on your network. After getting an idea of what the incident looks like, you can then drill down into individual events and files to investigate details at a granular level. Guided response, root cause analysis, and attack visualization make Threat Cases a one-of-a-kind experience for network administrators.
See where attacks originated, how and where they spread, and identify which files, processes, applications, and devices were affected by the breach. Threat Cases are available for both XG firewalls and for servers, offering extensive visibility and control both on-premise and in the cloud.
Quickly identify, diagnose, & mediate
-
- Isolate affected devices
- Search for similar threats
- Clean up after a breach
- Block threats with automated guided response
For example, if malicious behavior is detected in an Office 365 file such as a Word document or Excel spreadsheet, Sophos Threat Cases will indicate that the file was written to the computer by Outlook.exe and tip off administrators that the threat was the result of a malicious email. Admins may then use this information to identify and close security gaps to prevent future exploitation of this attack vector.
Threat cases are only generated for malicious behavior detections and do not include detection of Potential Unwanted Applications and other false positives.
Types of infections seen by Sophos Threat Cases:
-
- Malware detection
- Web threats
- Malicious behavior
- Malicious traffic
- Exploits
Where to find Sophos Threat Cases
If you want to take advantage of the features offered by Sophos Threat Cases such as root cause analysis, registry key and process filters, infection path visualization, and guided response, you’ll need an Intercept X Advanced license to get started. Once logged into your Sophos Central Admin dashboard, Sophos Threat Cases can be found by clicking the “Endpoint Protection” or “Server Protection” menu linked in the “My Products” section.
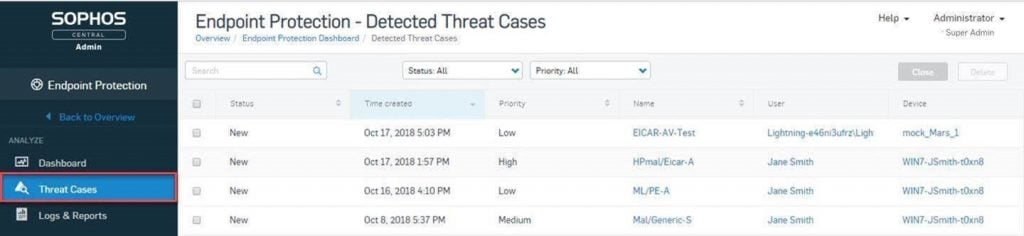

The Anatomy of a Threat Case
What does a threat case event look like and why is it so helpful for network administrators? Every Threat Case begins with a simplified events chain, giving an easy-to-follow visualization of the basic details of your incident.
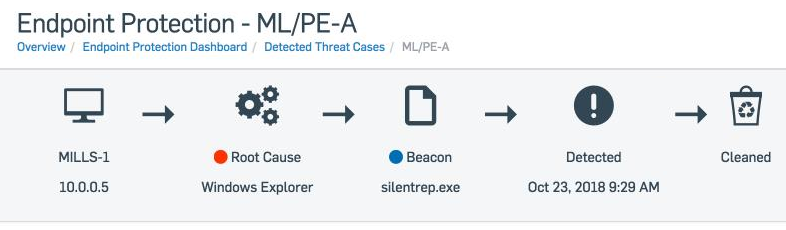

After the simplified attack chain, each Sophos Threat Case serves up a more robust attack summary that details basic information like detection name, root cause, potentially affected data, infected user, device names, and attack timeframe.
The summary section is followed up by a Suggested Next Steps function which generates automated remediation advice on what to do next. Advice is dependent on the type of attack and other details specific to the incident. Examples of some advice from Sophos Threat Cases include isolating computers, setting priorities, and setting the status of a case record.
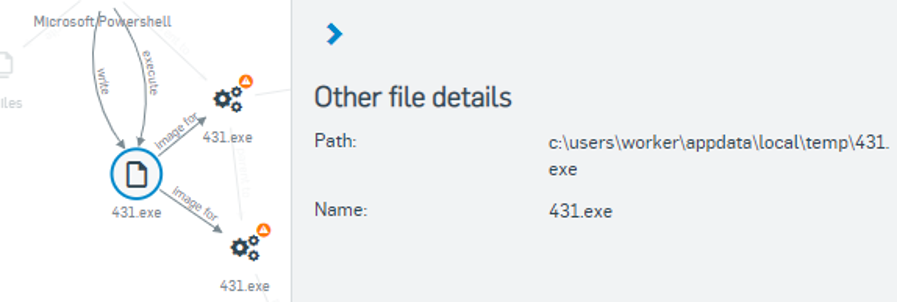
Last but definitely not least, the Analyze section is home to most of the detailed information admins will love from Sophos Threat Cases. Here you can find graphics of the attack “beacons” that Sophos detected and the root cause that Threat Cases identified. The beacon and root cause are then linked by interconnecting lines that make up the attack chain.
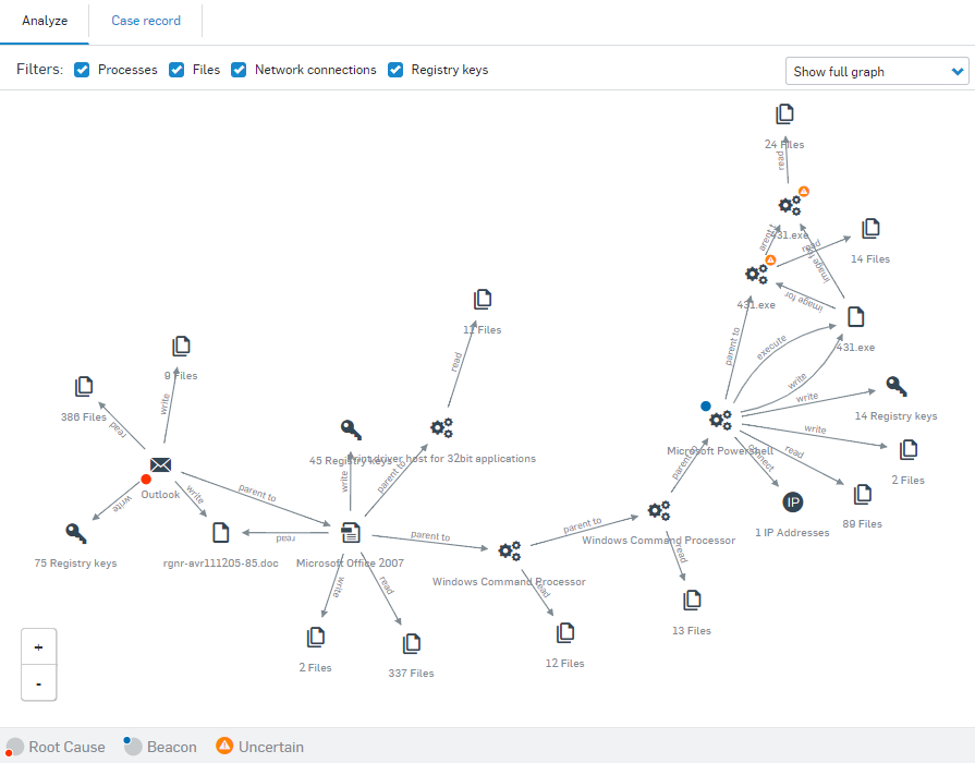

Admins can click on any individual event in this attack chain graphic, allowing them to view additional detailed information in a right-hand pop-up menu.

Try Sophos Intercept X and Sophos XG Firewall
Ready to get your hands on Threat Cases but still not sure about Sophos security? Try a 30-day trial of Intercept X or a 30-day trial of Sophos XG Firewall for free before you buy. You can also get your next Sophos XG Firewall appliance at no cost when you purchase a qualifying 3-year security license with our Sophos Evolved Firewall Promo.