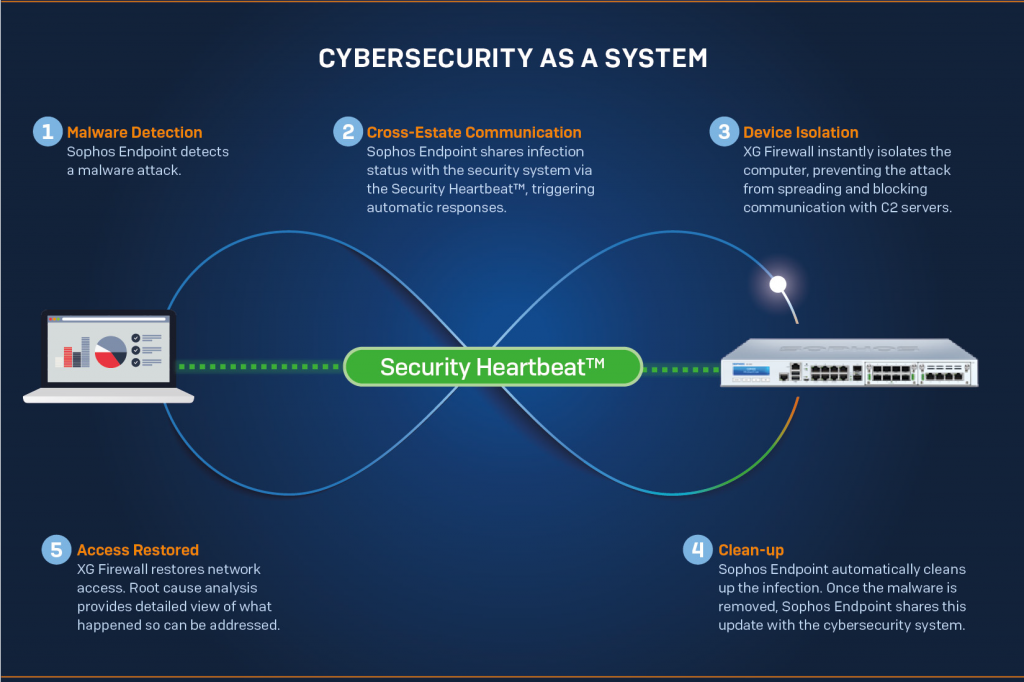
Sophos has long been known for creating holistic network security solutions that work across devices to provide broad views of network security posture. We have talked about the boons of Synchronized Security with Sophos Security Heartbeat for years on this blog! Now that cross-device monitoring and high-powered AI security goes a step further with the introduction of XDR.
What is XDR?
XDR stands for Extended Detection and Response. This sounds similar to another industry technology: EDR, or Endpoint Detection and Response. But XDR takes the concept of Endpoint Detection & Response and extends it across multiple security layers. It brings together real-time network data and automated decision-making to provide advanced threat responses that stop attacks before they become a breach.

How is Sophos XDR different from other solutions?
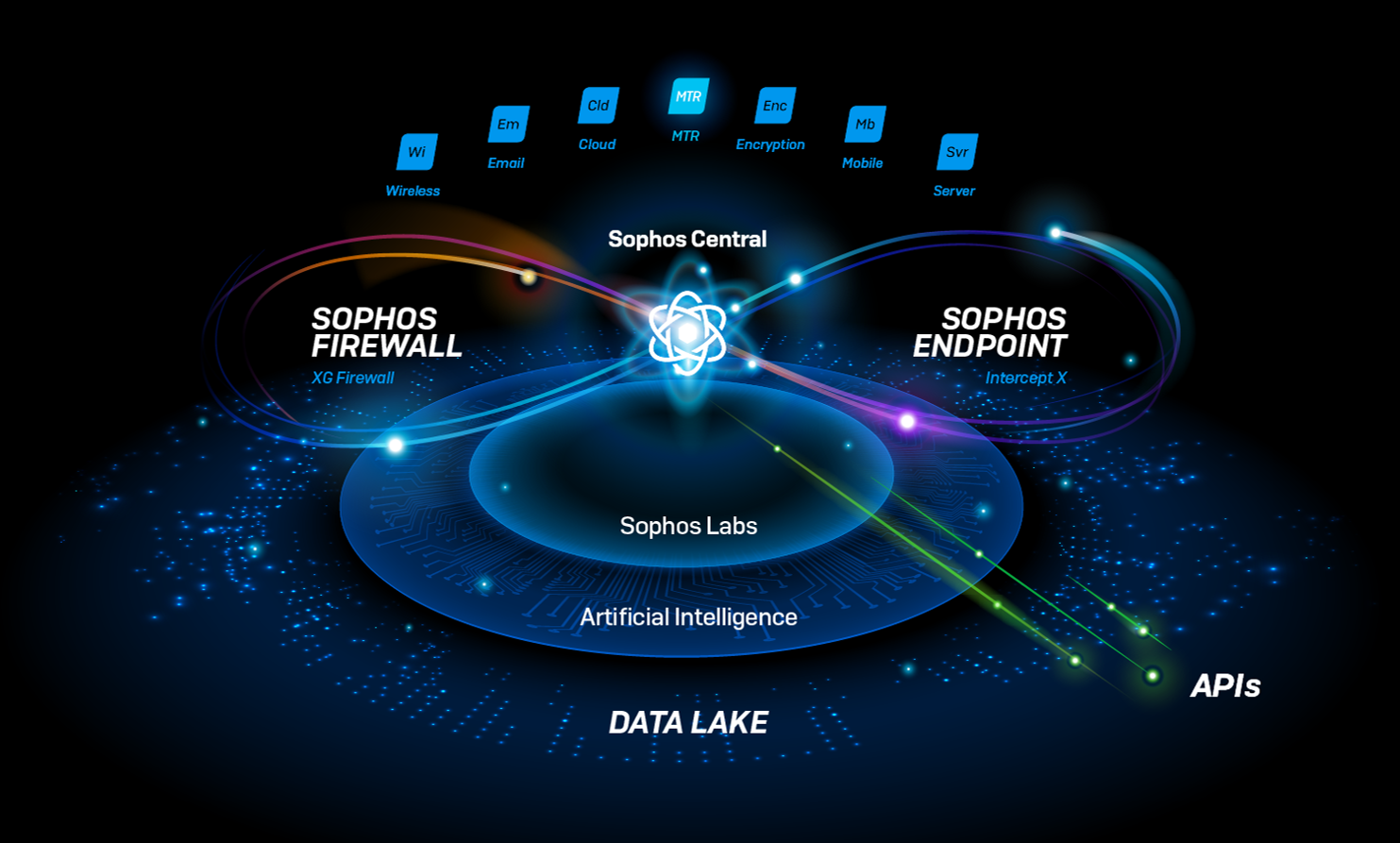
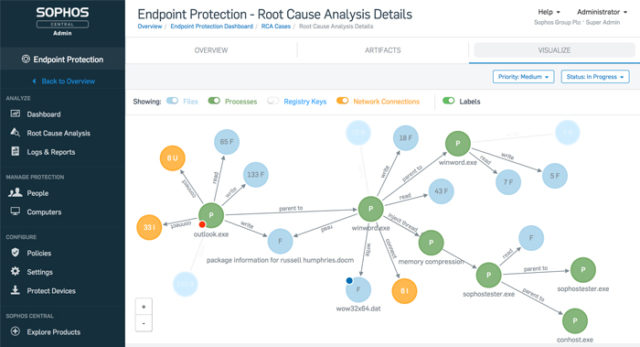
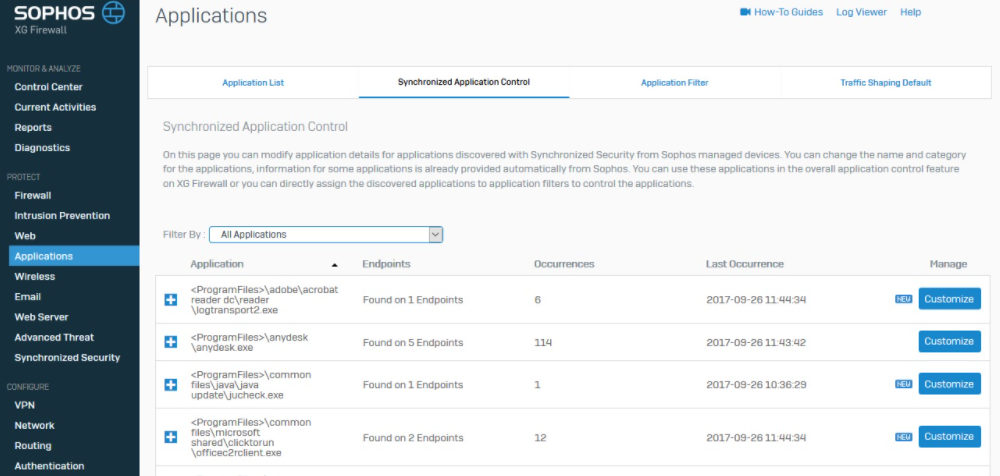
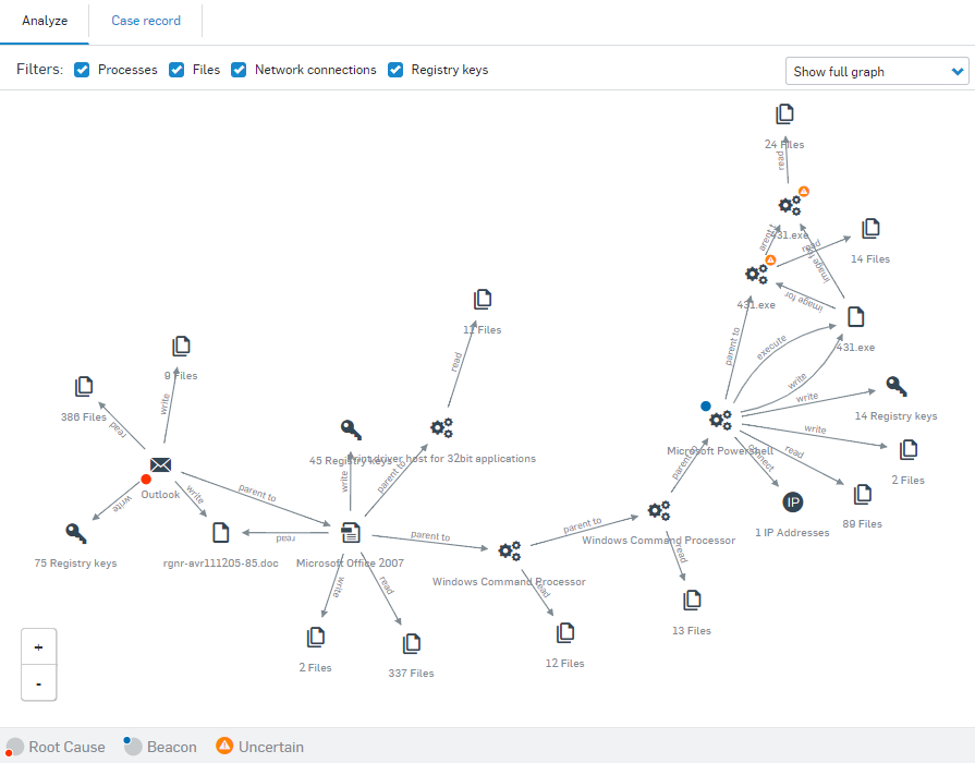
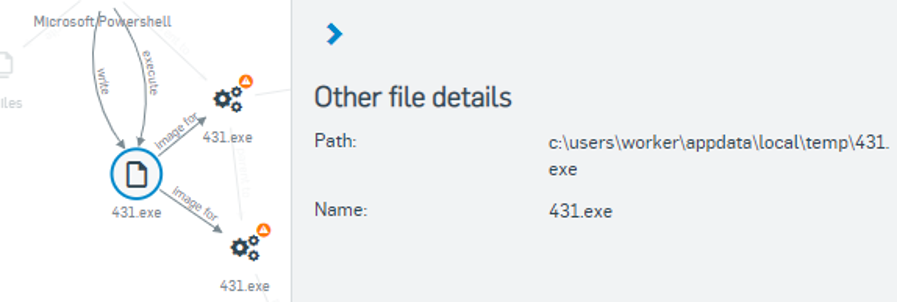
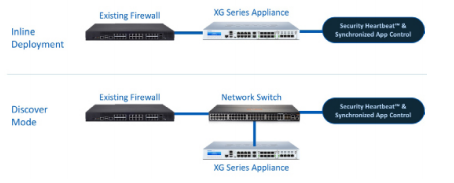
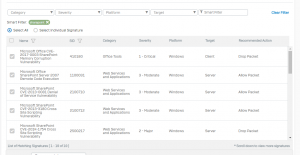
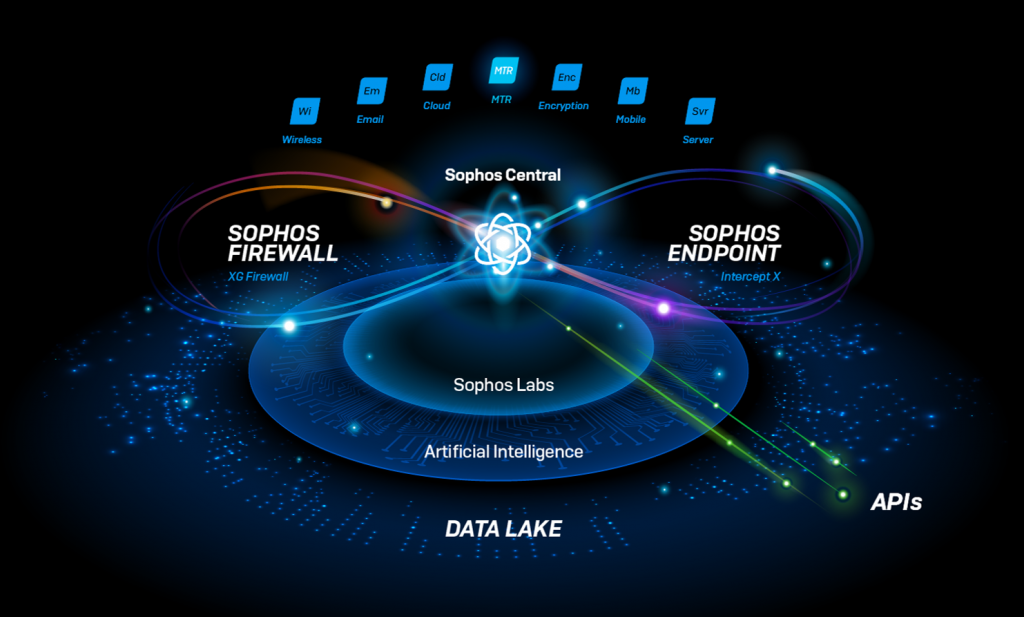
Sophos Intercept X Advanced with XDR (formerly Intercept X Advanced with EDR) integrates email, cloud, mobile, and endpoint data across your network, pulling data from multiple sources across security layers and products to provide broad, high-level security determinations orchestrated by deep learning AI. XDR leverages data from endpoints, servers, firewalls, switches, and other security devices spread across your network and centralizes that intelligence in a single ecosystem.
This pitch may sound familiar to you if you’ve used SOAR (Security Orchestration, Automation, & Response) or SIEM (Security Information & Event Management) solutions. What SOAR and SIEM do is quite similar in function: collect large volumes of data from multiple sources, analyze events, and provide guided response recommendations. Where XDR shines and soars above preceding solutions lies in its ability to take action. Sophos XDR not only creates a roadmap of how admins should respond to an event but takes the initiative to apply those steps before a security incident can grow.
All in all, XDR goes beyond data gathering and helpful suggestions. Sophos XDR orchestrates responses and applies them across devices on a network.
How to get Sophos XDR
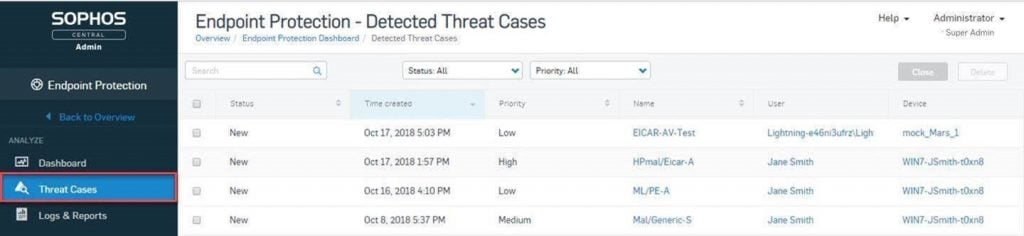
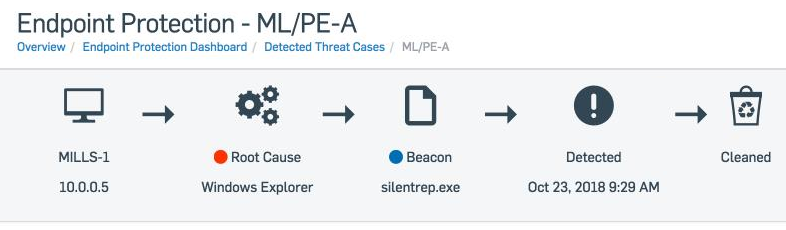
XDR found a home with Sophos as part of its Intercept X product suite, an advanced endpoint protection suite built to stop malware, ransomware, exploits, viruses, and zero-day threats. In previous years, Intercept X Advanced could be paired with EDR to automatically detect and prioritize threats. While Intercept X’s EDR capabilities suggest where and how network admins focus their attention, XDR is now fully closing the monitor-detect-respond decision-making loop.
Sophos Intercept X Advanced uses the latest machine learning technology to make security verdicts on unknown threats by comparing the behavior of potentially dangerous files or apps to the known behavior of currently understood threats.
Shop Sophos Intercept X Advanced with XDR
Try Sophos XDR for yourself
Try a free online demo of Sophos XDR and see how endpoint detection and response driven by AI can tie together the loose threads of your network.