What is Synchronized Security?
Synchronized Security is a system designed by Sophos to address a glaring shortcoming in most cybersecurity environments: lack of coordination. Security companies tend to focus on developing individual products to address specific points of attack, often ignoring the bigger picture of holistic network security. These old-school approaches to cybersecurity are complex, short-sighted, and composed of several disparate moving parts. As organizations adopt more and more security solutions, they slowly build their own InfoSec-version of Frankenstein’s monster. For those of you who haven’t read the famous tale, it doesn’t turn out that well.
What Does Synchronized Security Include?
Synchronized Security allows the individual aspects of your security setup to communicate in real time and make decisions based on complete context. Here’s a closer look at some of the handy features that make up Synchronized Security:
Sophos Security Heartbeat – A secure communication link that allows Sophos products to communicate and share information about your network health. In mere seconds, the Security Heartbeat can detect, judge, and respond to incidents on your network; a process which once took hours to complete while your network was left in limbo.
Synchronized App Control – Providing instant insights into unidentified software, Synchronized App Control grants the level of detailed oversight that administrators crave. This includes the ability to map unknown applications, organize them into categories, and prioritize bandwidth for mission-critical processes. Watch this Sophos video on Synchronized App Control to learn more.
Sophos Central – A security platform through which network administrators can manage all Sophos products and protections on one screen. This smooth, intuitive dashboard comes with convenient “traffic signal” indicators that instantly identify the status of your security: green is good, yellow is cautionary, and red means an issue needs your attention.
Automated Incident Response – Incident response used to take hours, days, or even weeks. Sophos transformed this process into a sub-minute affair with Automated Incident Response. Information is shared across your security system to make instantaneous decisions about suspicious activity. Infected endpoints are isolated before threats can spread, shutting down both east/west and vertical movement.
Add Synchronized Security to Any Existing Network
By now you may be thinking “This sounds great, but I already have an established network with a different brand of firewall.” You’re in luck! Synchronized Security can be bolted onto your existing network, expanding and improving your current security capabilities. All you need to enable Synchronized Security is an XG Firewall installed on your network. This can be deployed in two configurations: as an Inline appliance in bridge mode or in Discover mode (TAP mode) through a mirror port. Either method can be done in just a few minutes with Sophos’ step-by-step deployment wizard.
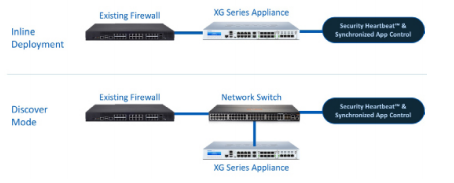

Inline vs Discover Mode
Discover Mode
A Discover Mode deployment is the least intrusive method, offering a risk-free way to increase visibility of unknown applications. By connecting an XG Firewall to a mirror port on a network switch, you start receiving valuable insight immediately. Though you will be unable to add more advanced Sophos security controls in Discover Mode (like sandboxing & web server protection), these insights position you for a greater understanding of your true network traffic.
Inline Mode
An inline deployment sheds even brighter light on your network, serving up unparalleled application visibility. By deploying an XG Firewall “behind” your current appliance, you gain Security Heartbeat, Synchronized App Control, & Automated Incident Response. The flexibility offered by fail-open bypass ports enable deployment of an XG Firewall in bridge mode, allowing traffic to flow without disruption even if the appliance needs to be shut down or rebooted.
What’s In It For Me?
- Fewer unknown threats hiding on your network.
- Automated Incident Response to isolate infections before they spread.
- Effortless endpoint health monitoring with Security Heartbeat.
- Plus, you can try it out risk-free for 30 days.
Sophos will ship you an XG Firewall to test out for free, letting you explore Synchronized Security for yourself. Not impressed? Just ship it back.












