
Exploring Fortinet's FortiGate Models:
Your Comprehensive Guide to FortiGate Firewalls
If you are in the market for a robust firewall that will shield your network infrastructure from cyber threats, Fortinet’s FortiGate Firewalls are a great option. Fortinet’s range of FortiGate models are tailored to meet your specific business needs and provide advanced security features, high performance and scalability. Let’s dive into the world of FortiGate models and discuss their key features and benefits, the differences between Fortinet firewall models, and what you need to know before choosing which model to purchase.
Understanding FortiGate Firewalls
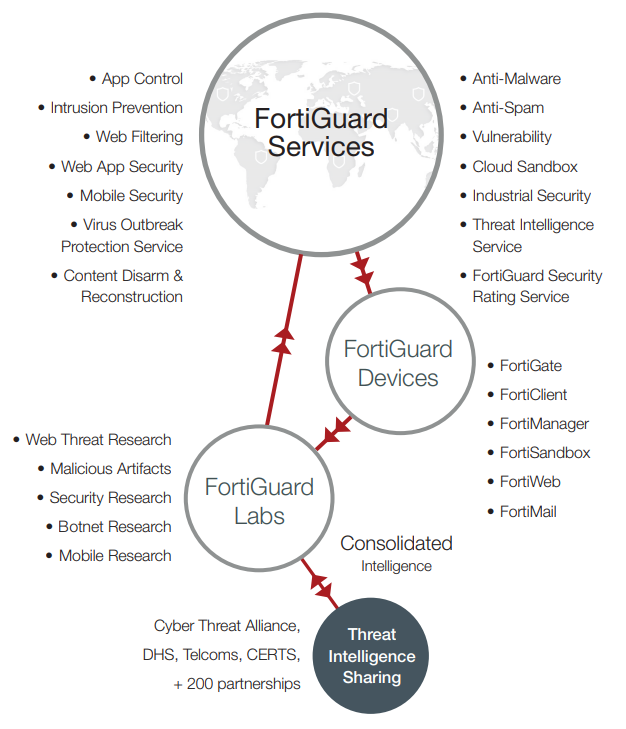
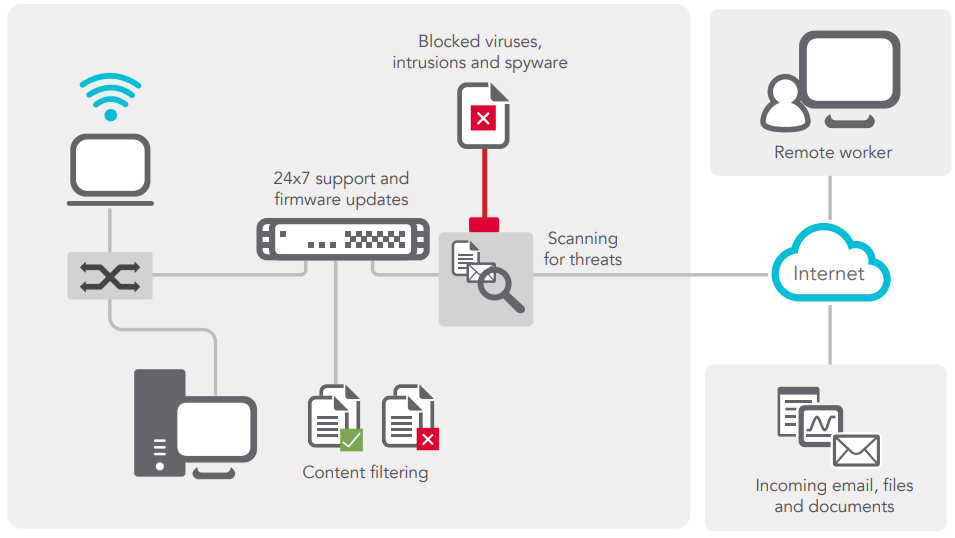
Fortinet FortiGate firewalls are the first line of defense of Fortinet’s comprehensive security platform. FortiGate models are Next-Generation Firewalls (NGFW) that are designed to protect networks of all sizes: home offices, small to medium sized businesses, enterprises and more. These devices combine essential security functions such as intrusion prevention, antivirus, web filtering, and application control into a single piece of equipment.
Key Features of FortiGate Models
FortiGate Models come in several different sizes and are able to be custom configured, catering to the diverse needs of all kinds of networks. Here are some key features you can expect across the FortiGate product line:
- High Performance: Fortigate firewalls deliver high throughput and low latency, ensuring network traffic is processed efficiently without compromising performance.
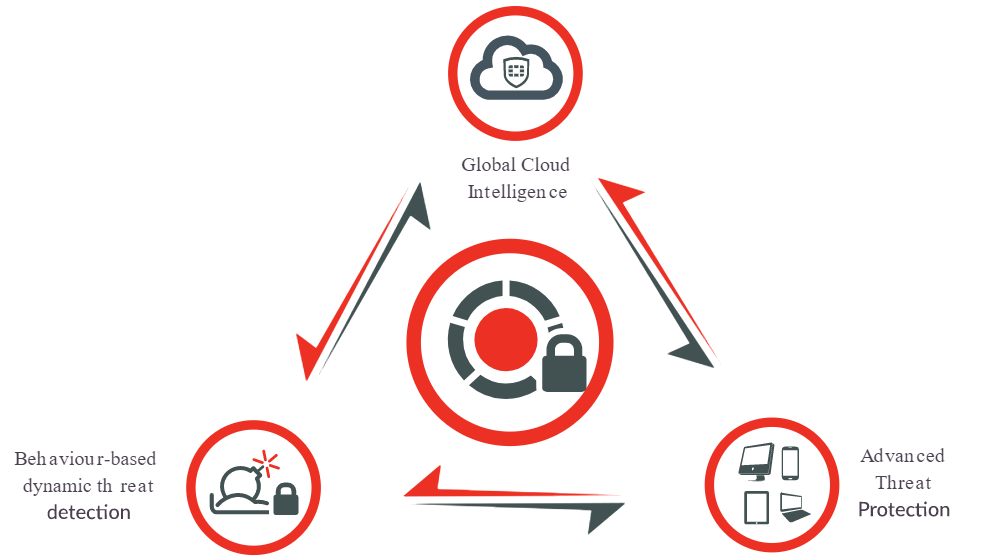
- Advanced Threat Protection: FortiGate models come equipped with advanced threat detection and prevention capabilities. Some of these capabilities include sandboxing, botnet detection, and AI-driven threat intelligence.
- Centralized Management: FortiGate firewalls can be centrally managed through Fortinet’s FortiManager platform, allowing administrators to to configure, monitor and analyze security policies all in one place.
- Secure SD-WAN Integration: FortiGate models seamlessly incorporate security into SD-WAN deployments, establishing secure connectivity across distributed networks.
- Scalability: Fortinet’s large selection of FortiGate models offers scalability to fit growing network demands without jeopardizing security or performance.
Things To Consider When Purchasing a FortiGate Firewall
There are several factors that can help determine which FortiGate model to buy. Listed below are some of the basic components to consider when choosing which firewall will best suit your needs.
- Recommended User Counts – This might be the most important aspect when it comes to picking a firewall model. Whichever firewall you purchase must be able to support the number of users on your network. A user is defined as any desktop, laptop, printer, phone, tablet, or other internet-connected device operating on your business’s network. We recommend choosing a firewall with a larger user count than you need so your business has room to expand and can easily handle resource-heavy applications.
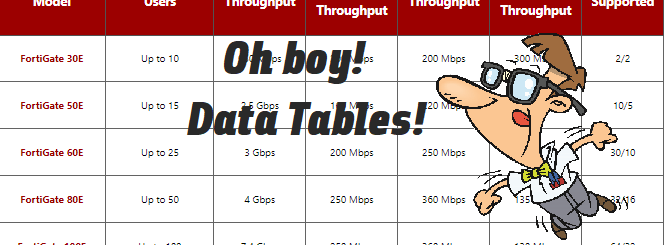
- Throughput Speeds – A firewall’s throughput speed is a measure of internet traffic volume that can pass through the firewall at any one time, based on the processing power of the hardware. Throughput is measured in Mbps (megabits per second) and Gbps (gigabits per second). Fortinet data sheets list a variety of throughput speed statistics for you to look through.
- SSL VPN Throughput – Secure Socket Layer (SSL) and Virtual Private Networks (VPN) refer to communication protocols that govern how information is encrypted and transmitted between a source and its destination. Using SSL VPN tunnels is the most secure means for remote workers, outposts, and branch offices to access resources from the primary database.
- Site-to-Site VPN Tunnels – Site-to-Site VPN tunnels allow fixed-location Local Area Networks (LANs) to extend secure conduits to the main office intranet. FortiGate datasheets outline the maximum number of tunnels that a firewall can accept from remote LANs.
- Form Factor – The form factor refers to the size and shape of the firewall. Most firewalls will have either a desktop or rackmount form factor. A firewall with a desktop form factor implies that the firewall is compact enough to comfortably sit atop a desk, while a rackmount form factor means the appliance was designed to be secured in a standard server rack. If the firewall you need has a rackmount form factor, you can easily purchase the coordinating rackmount on our site.
- Wireless Support – Some businesses prefer wireless firewalls instead of firewalls that must be connected via Cat5E/Cat6 cabling. Although wired appliances are generally faster and more stable, wireless firewalls are still a good and viable option for organizations needing more flexibility and a faster deployment. FortiGate wireless firewalls, or FortiWiFi firewalls, are able to reach any location without the limitations of physical cables and require less equipment and planning.
List of Fortinet FortiGate Models / Series
Below is a list of all the FortiGate models Firewalls.com sells. You can click on each series to view all the product offerings, download data sheets, and compare the specs and features.
Popular FortiGate Models We Recommend
- FortiGate 40F: This model is our go to for customers that own small businesses or have home offices / smaller retail locations. The FortiGate 40F offers a compact form factor with robust security features, providing your small business with enterprise grade security.
Download FG-40F Data Sheet - FortiGate 200F: We recommend this model for mid-sized businesses or enterprises. The FortiGate 200F delivers high-performance security with advanced threat protection capabilities, making it perfect for distributed environments and regional offices.
Download FG-200F Data Sheet
Licensing For Your FortiGate Firewall
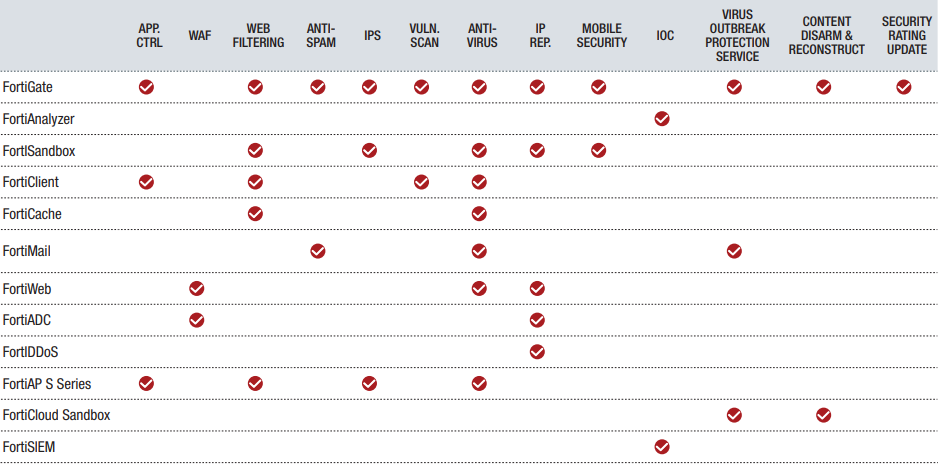
Fortinet offers many security add-ons and upgrades to further secure your network. These licenses may be either a one-time upgrade or a recurring subscription. If you would like to save time and money, you can opt for a 3 or 5 year license that is bundled with your FortiGate firewall. Here are a few examples of additional licenses Fortinet offers for FortiGate Firewalls:
- 24×7 FortiCare Contract – This subscription includes technical support 24×7, 365 days a year. It also includes advanced replacement service for hardware failures.
- Advanced Threat Protection – This service enables Fortinet Security Fabric to use integrated detection of advanced threats for automated response & mitigation.
- FortiCloud Management & Analysis – This subscription grants access to Fortinet’s Cloud Management platform for simplified deployment, setup and management of your devices.
- FortiGuard Advanced Malware Protection – This license combines antivirus, mobile malware and FortiSandbox Cloud service
- FortiGuard Web Filtering Service – Subscription-based managed web filtering solution that sorts billions of webpages & sites into categories to be allowed, restricted, or blocked.
Let Us Help Choose The Right FortiGate Model For You
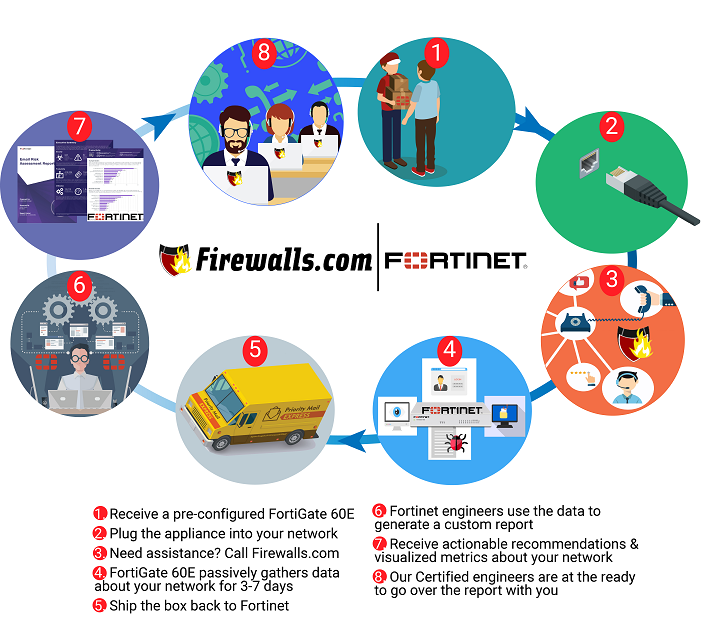
You might be experiencing information overload after reading everything above, and that’s totally understandable! We have security experts that will walk you through choosing the best FortiGate Model for your business as well as deploying and managing your device if you need it. Firewalls.com’s in-house team of certified network engineers can help decipher which firewall you need as well as custom configure your firewall to optimize your network security.
Learn more about Firewalls.com Configurations
The Firewalls.com Managed Services team can also monitor, report and mitigate attacks on your network around the clock. This service is great for businesses that may not have enough IT staff to dedicate to managing your devices and network.
Learn more about Managed Services
Still Not Sure About FortiGate Firewalls?
Let’s face it: cybersecurity is complicated. Firewalls.com encourages you to make an informed decision when purchasing any firewall because when the bad guys lose, we all win. Our account executives provide a low-pressure experience that’s heavy on product expertise and backed by decades of experience. Firewalls.com wants you to be 100% confident in your network security investment before any transactions begin.